Delivery is an “Easy” machine on Hack the Box. Check out its official page for more information, or to start it up and follow along.
System Scan #
As always, fire up nmap and do a scan of the sytem.
sudo nmap -sS -sV -sC -p- 10.10.10.222 | tee nmap-scan.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-27 18:23 EST
Nmap scan report for 10.10.10.222
Host is up (0.048s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 155.96 seconds
I suggest you run this nmap command on your local machine, since I’ve cleaned up the output a bit for formatting.
For an nmap primer, you can
check out this site.
If you’re new to nmap and are curious about the flags, here’s what they all do.
-sSfor stealth scanning-sVto get versions of services-sCrun common scripts-p-on all ports
The scan found three services running:
- 22: SSH; Usually not exploitable, but good to know if credentials are obtained.
- 80: Web server; Biggest attack vector. Needs further enumeration.
- 8065: Unknown Service; Looks like some form of web service according to the nmap scripts ran against it.
Start with the biggest attack vector, and enumerate the web site running on port 80.
Enumeration: Web Site #
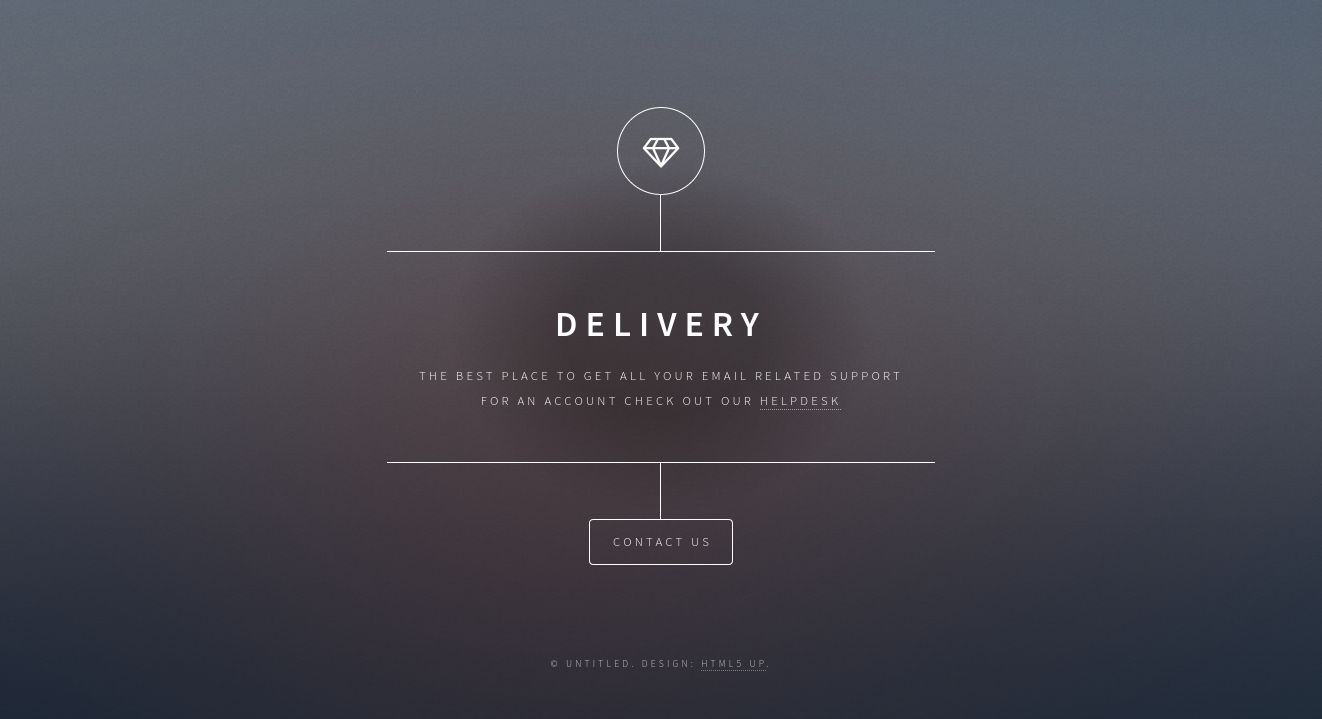
A basic landing page with information about a delivery company. There is not much to go on here. Reading the content and viewing the Contact section, there are a few links to other services:
Since .htb is not a real top level domain, and :8065 was the unknown service that nmap reported, it’s a safe assumption that these are local to this machine.
Sad thing is, the links don’t work!
This can be fixed though!
We can edit the /etc/hosts file on our Kali box to tell the web browser that any DNS resolution of those URLs should point to the IP address of the HTB server.
# add to /etc/hosts
10.10.10.222 delivery.htb
10.10.10.222 helpdesk.delivery.htb
We can now go to http://delivery.htb/ and it will display the same landing page as before. Going to the other external links, we find two other services running on this box.
- HelpDesk: osTicket Support Ticket System
- MatterMost (the unknown service running on 8065)
MatterMost sounds pretty interesting, so let’s start with that.
Enumeration: MatterMost #
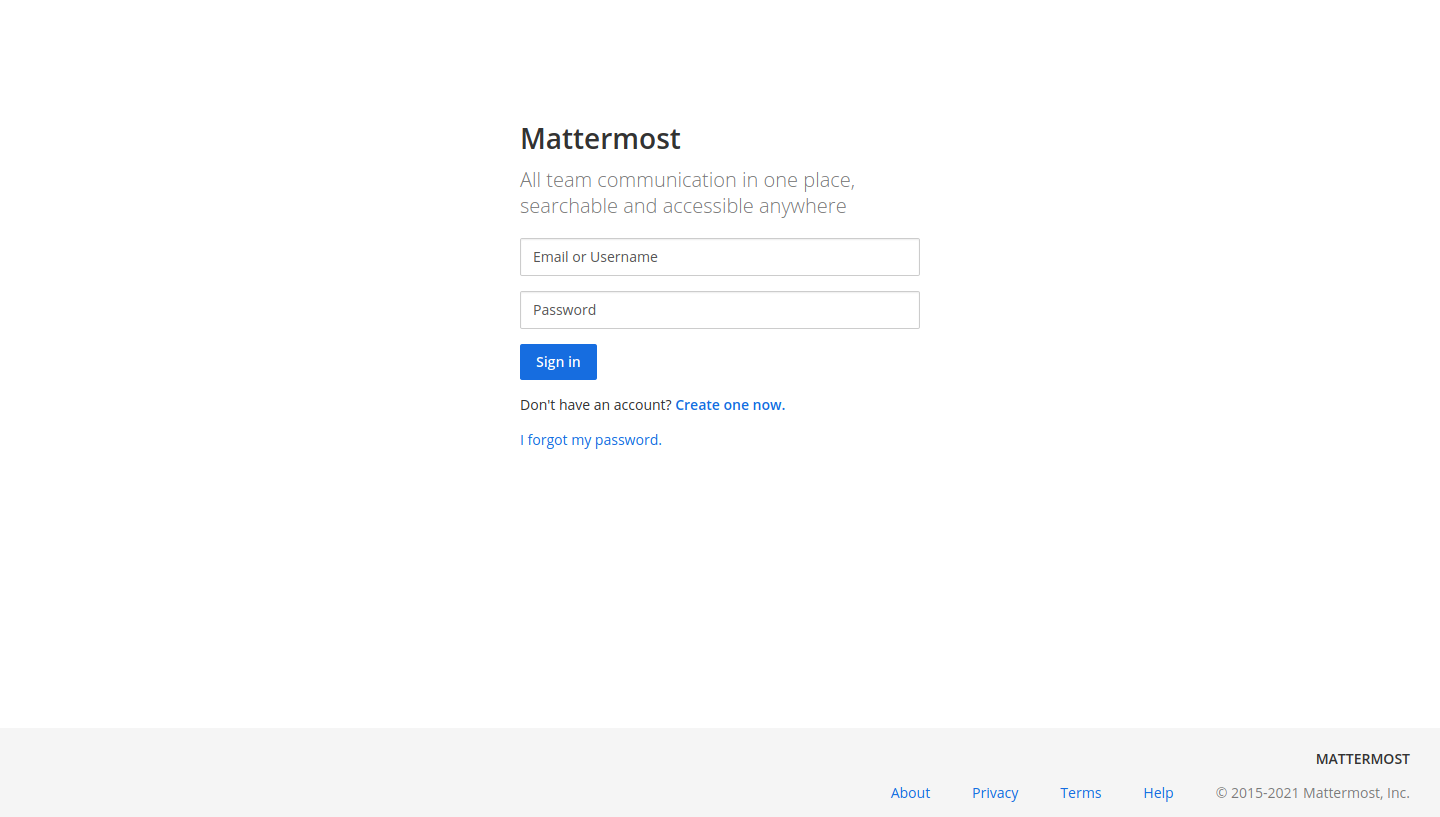
What is MatterMost?
MatterMost is an open-source, self-hostable online chat service with file sharing, search, and integrations. It is designed as an internal chat for organisations and companies, and mostly markets itself as an open-source alternative to Slack and Microsoft Teams.
This is a fairly new piece of software, written in Go. There’s nothing related to MatterMost on ExploitDB (at the time of writing), and the only article I found about exploiting MatterMost seems to reference an older version, and is from a few years back. Not too much to go on here for public exploits.
A quick glance at the service, though, it looks like it has open registration. We can try to register an account and view the channels on the system. Filling out some basic information, we can create a user…
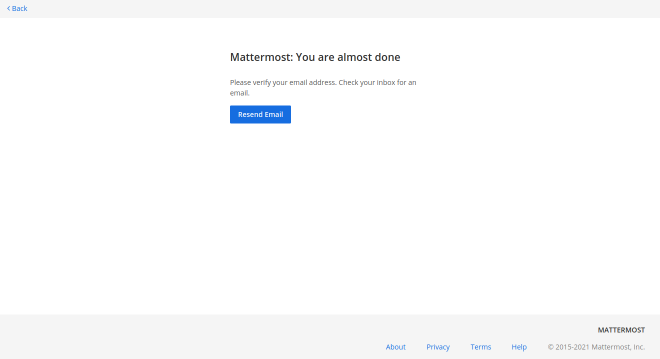
but need to verify our account. This is a default setting in MatterMost. That’s a shame. Not much we can do. Without knowing the code, or a valid email, there’s no way (that I could find) to bypass the email verification. Machines on HTB won’t send emails out (I tried using a throw-away email). Remember, don’t put PII on these publicly available machines.
Looks like we’ve hit a dead-end. Time to circle-back and investigate the Help Desk service.
Enumeration: Help Desk #
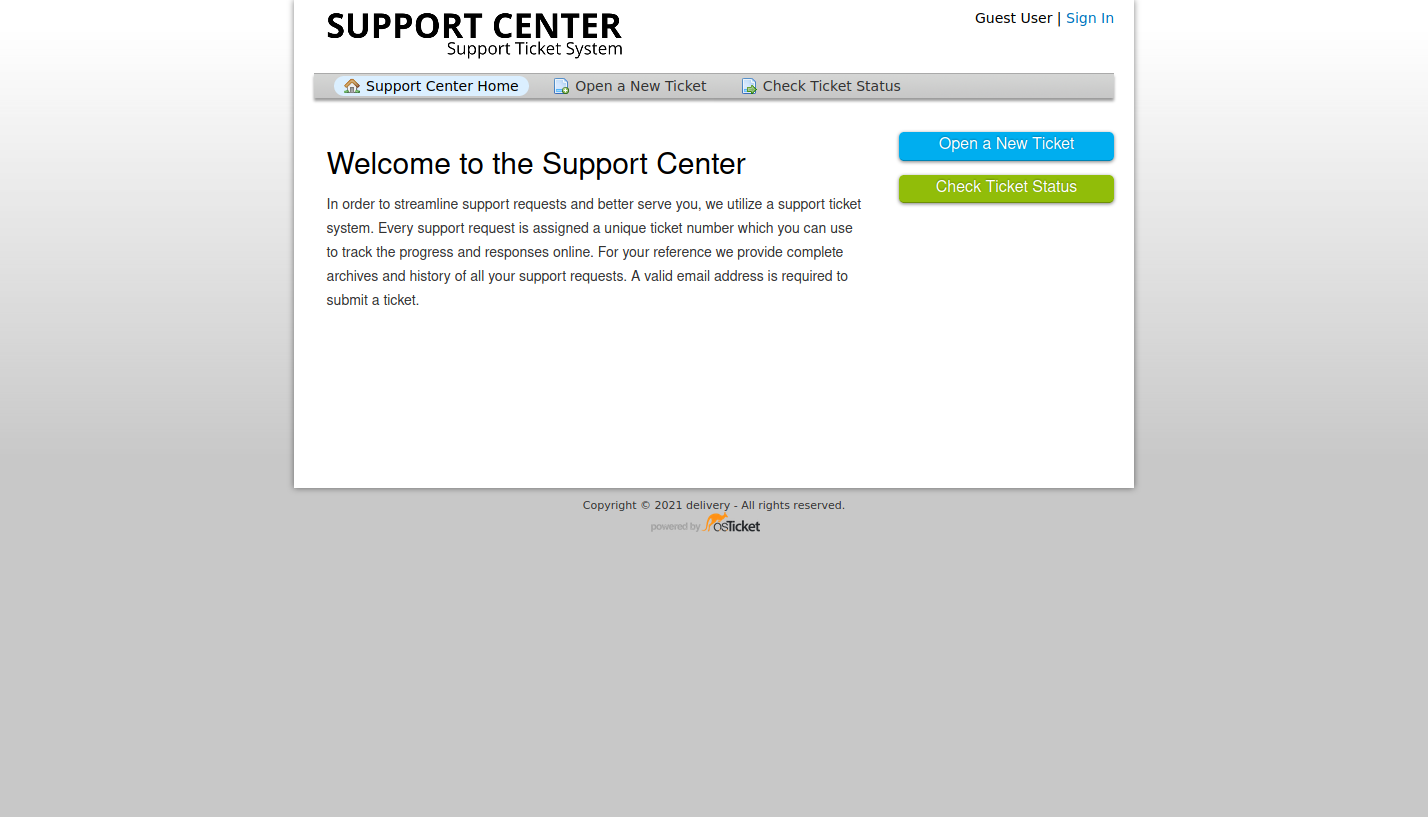
This looks to be powered by osTicket’s Support Ticket System. A widely-used and trusted open source support ticketing system. Can’t determine which version of the software it’s currently running. There are a handful of exploits on ExploitDB, but it doesn’t look like they are applicable to our situation. Other than trying to log in, the only other interaction is to Open a Ticket.
Rereading the Contact Us Section of the main website, it says to access the MatterMost service, one needs to get in touch with the HelpDesk.
For unregistered users, please use our HelpDesk to get in touch with our team. Once you have an @delivery.htb email address, you’ll be able to have access to our MatterMost server.
Go through the motions to create a ticket.
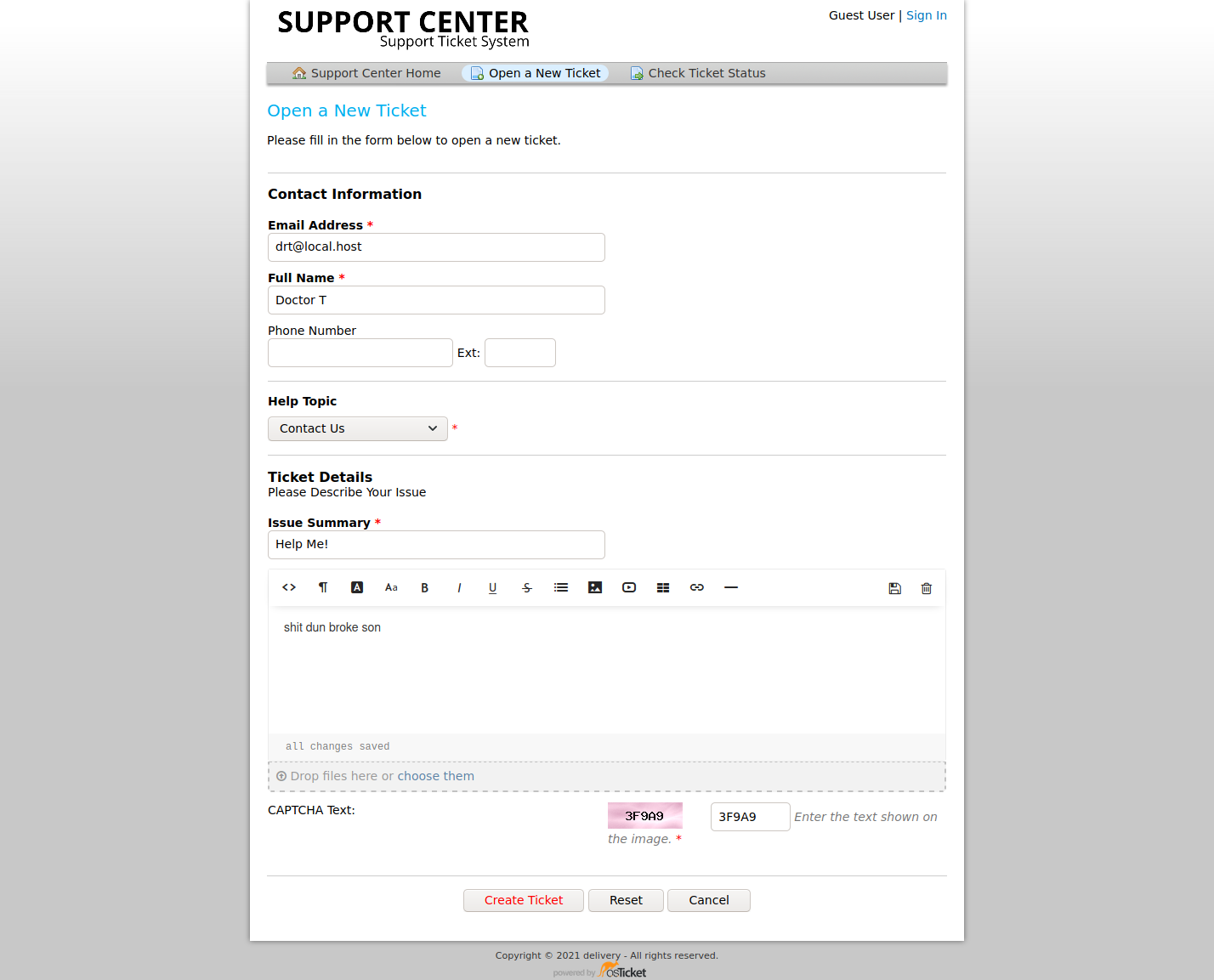
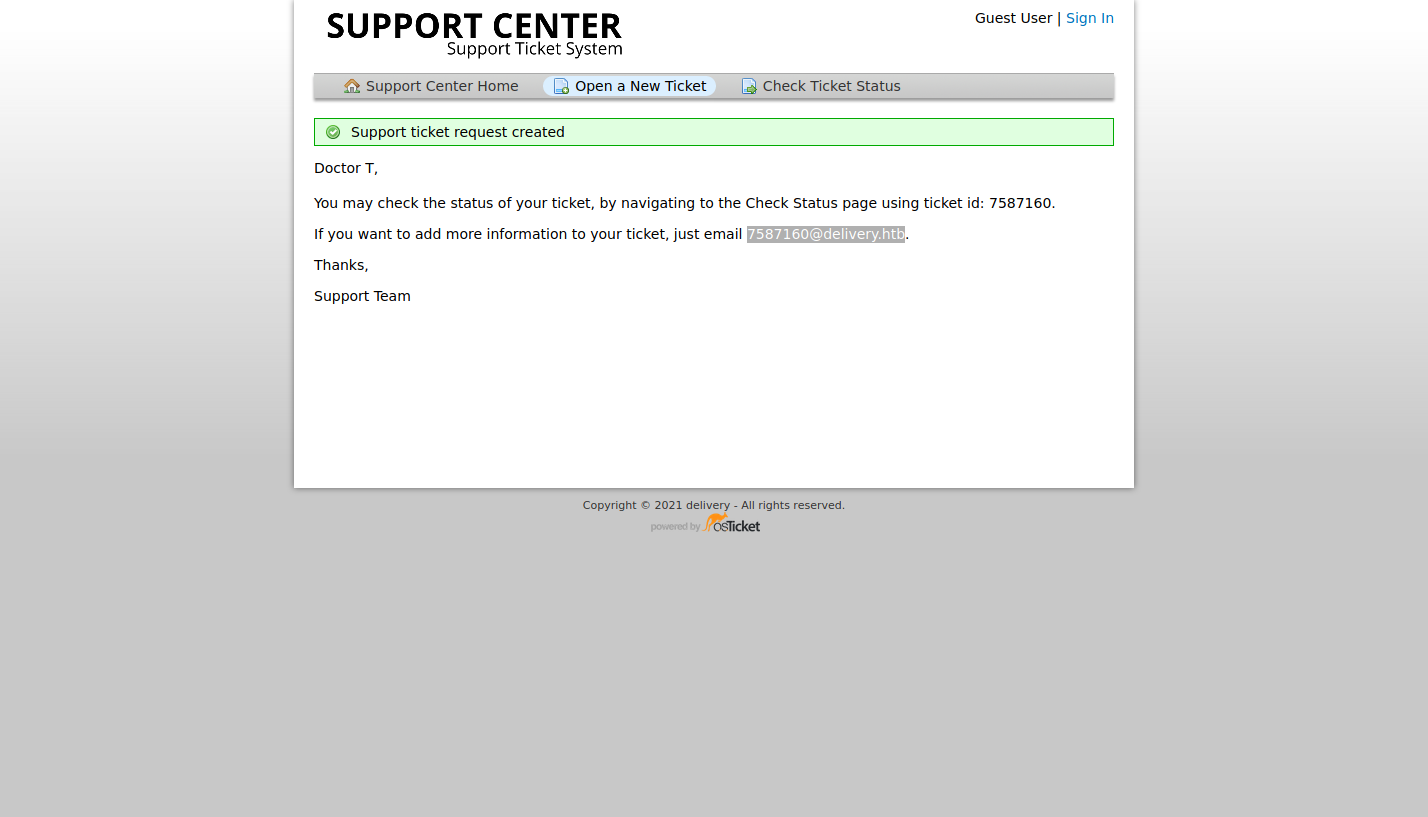
Look at that!
We have a @delivery.htb email address we can use!
This is very common of ticketing systems.
Allowing the customer to reply directly to an email, and it will show up in the Customer Service Portal.
Let’s leverage this “feature”, to gain access to the MatterMost service!
Accessing MatterMost #
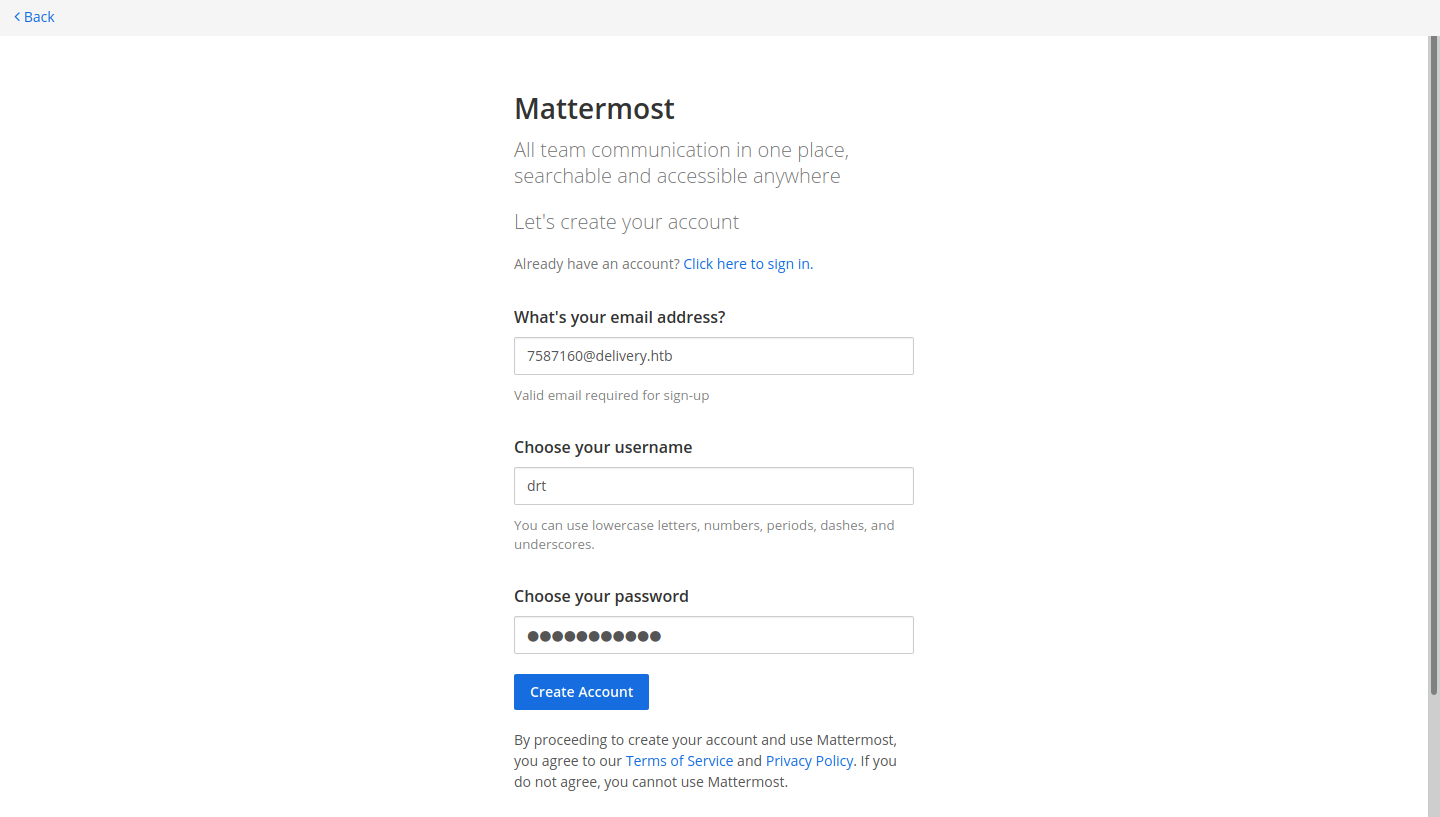
Based on our enumeration, and according to the website, we’ll need an @delivery.htb email address.
Thanks to the Help Desk ticket we created, we have now a valid email address to work with.
Sign up for a new user using the email from the support ticket.
To get the confirmation email, we’ll need to access the support ticket created earlier. Going back to the Help Desk, and use the Check Ticket Status option. View the ticket, use the ticket ID and the customer email ( [email protected]) to view the data.
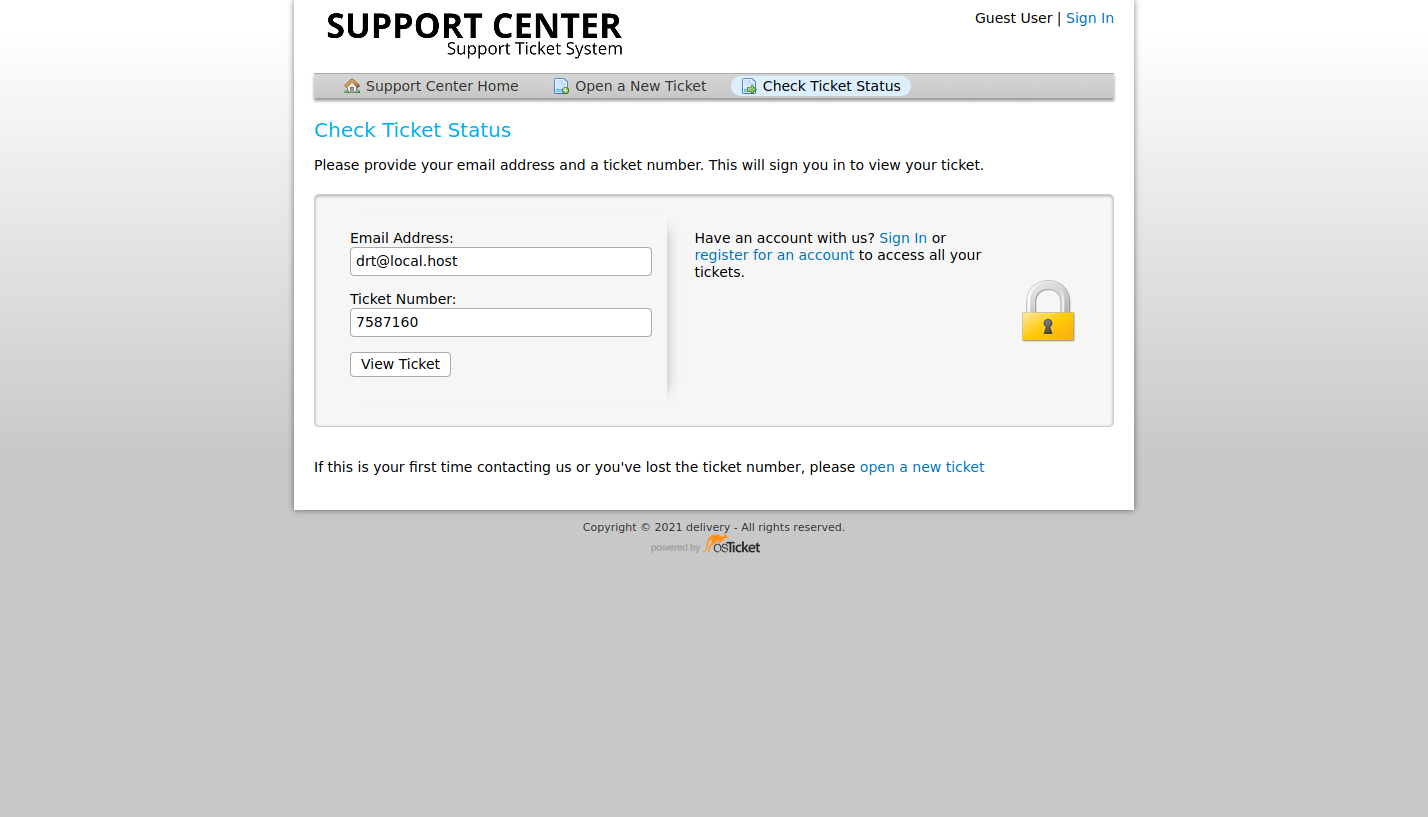
Check the page for the confirmation link to MatterMost.
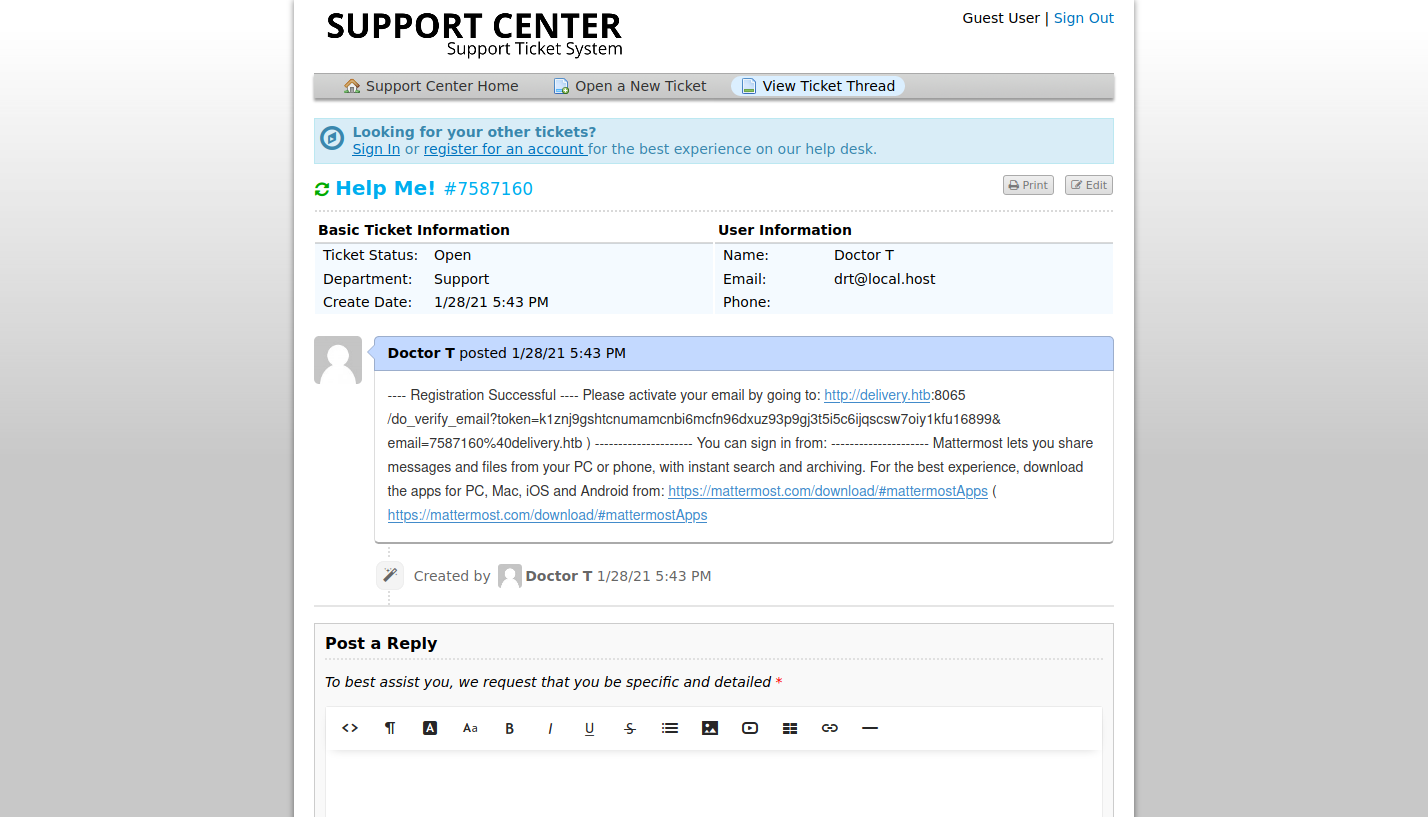
Copy/paste the confirmation URL into the web browser and gain access to the MatterMost instance.
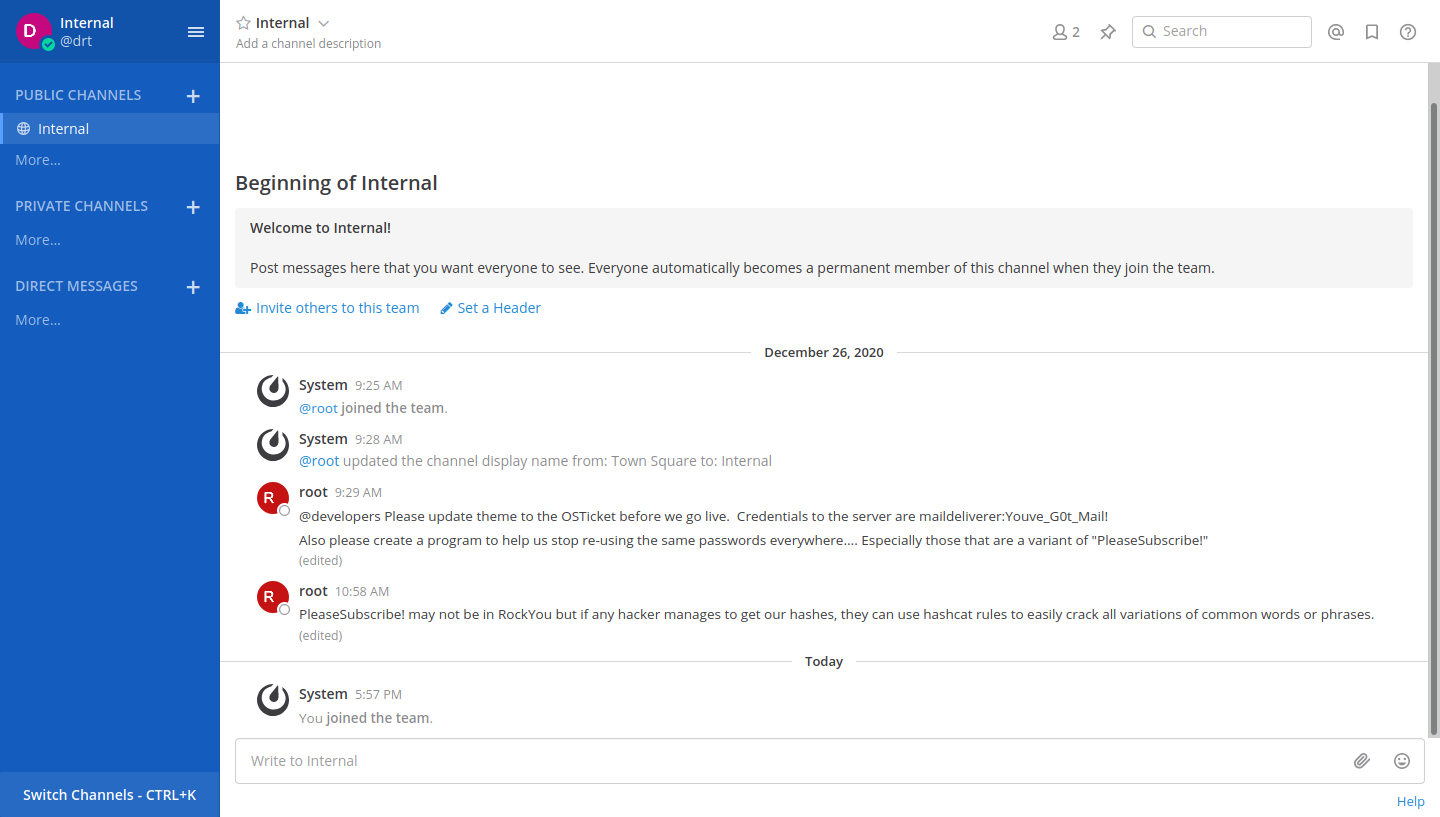
Looking at the thread we see one other user root and some SSH credentials.
There’s also a message to stop using a common password variation because of how easily it can be exploited.
Write this tidbit of information down for now.
Let’s try accessing the box using the SSH credentials provided in the thread.
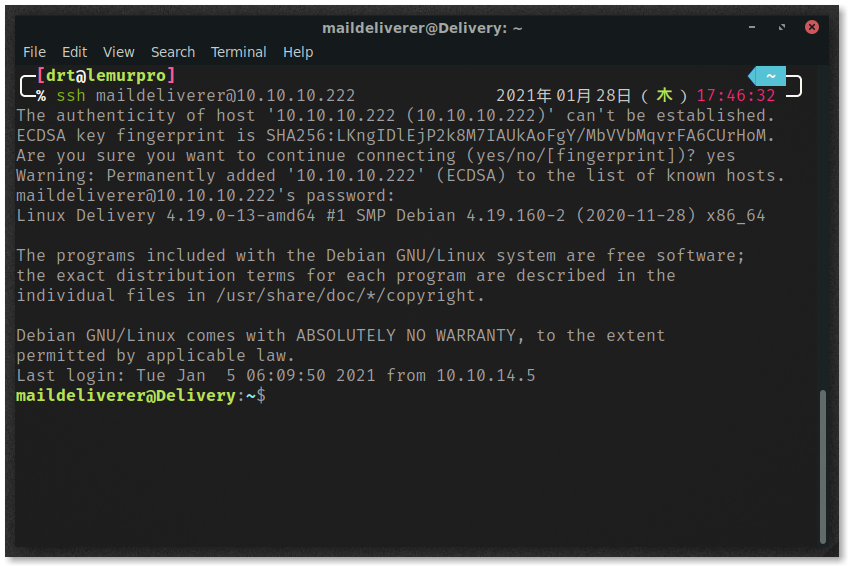
Success! We can now view user.txt

That’s enough partying for now, time to root the machine.
Server Enumeration and Privilege Escalation #
The maildeliverer user is a basic user, with no sudo privileges.
There are no obvious services that are running on the box as root.
However, there is a MySQL database running.
Which makes sense.
The ticketing system needs a way to store data, and it wouldn’t surprise me if MatterMost used a DB on the back end as well.
After some failed attempts, the maildeliverer can’t log into the database, and root account is password protected.
We’ll need to hunt for the database credentials on the system.
The MatterMost configuration file is located in /opt/mattermost/config/config.json and contains credentials to the MySQL database under SqlSettings.
The username and pass are in plain-text and can be used to log in to the database.
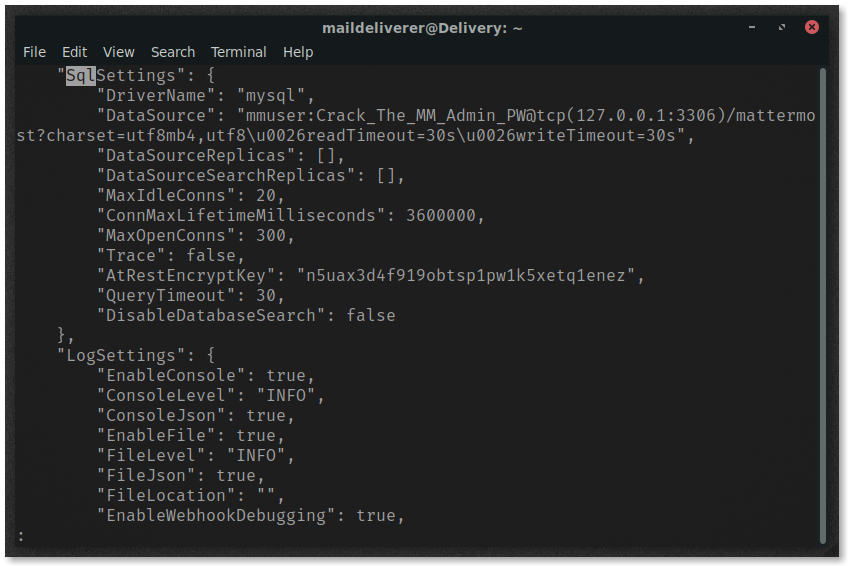
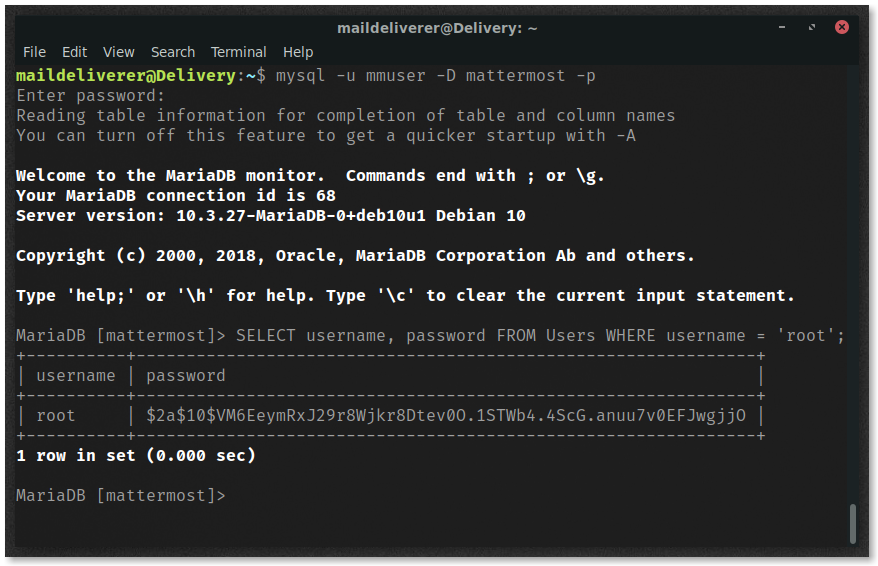
Access the database by executing
mysql -u mmuser -D mattermost -p
Obtain the username and password of the only other user on the MatterMost instance.
SELECT username, password FROM Users WHERE username = 'root';
We can now see the hash of the root user’s password!
Save this to a file called hash.txt.
Cracking the Password with hashcat
#
The next task at hand is to crack the hash of the root user’s MatterMost password.
Remember the comment that was made on the MatterMost channel?
Also please create a program to help us stop re-using the same passwords everywhere…. Especially those that are a variant of “PleaseSubscribe!”
PleaseSubscribe! may not be in RockYou but if any hacker manages to get our hashes, they can use hashcat rules to easily crack all variations of common words or phrases.
You see where this is going, right?
We’re going to use PleaseSubscribe! as our wordlist.
Create a new file called wordlist.txt and add PleaseSubscribe! to it.
We’ll have hashcat do a rule based attack to try and find the password.
Identifying the Hash Type #
Before we can attempt to crack the password, we need to figure out what type of hash this is.
We’ll need to provide the mode for hashcat, but more on that later.
To identify the hash, I am a fan of using hashid.
Fire it up in your terminal, run it, and at the prompt paste the hash.
hashid
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Analyzing '$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
Great we know that we need to use the
bcrypt hash mode in hashcat.
Flipping through the man page, we can see that this is mode 3200.
Hashcat Rules #
Stole from the Hashcat Wiki page:
The rule-based attack is one of the most complicated of all the attack modes. The reason for this is very simple. The rule-based attack is like a programming language designed for password candidate generation.
If you’re interested in creating your own custom rules, check out the documentation page. Hashcat comes with a few predefined rules you can use, but I decided to go with Hob0Rules on Github.
git clone [email protected]:praetorian-inc/Hob0Rules.git
Putting It All Together #
Here is the command and output from hashcat.
I’ve changed the password, you’ll have to take a crack at it yourself 😜
hashcat -a 0 -m 3200 hash.txt wordlist.txt -r Hob0Rules/d3adhob0.rule -o cracked.txt -w 3 -O
Session..........: hashcat # Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Wed Jan 27 12:47:22 2021 (42 mins, 34 secs)
Time.Estimated...: Wed Jan 27 13:29:56 2021 (0 secs)
Guess.Base.......: File (wordlist.txt)
Guess.Mod........: Rules (Hob0Rules/d3adhob0.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 16 H/s (3.88ms) @ Accel:16 Loops:64 Thr:1 Vec:16
Recovered........: 1/1 (100.00%) Digests
Progress.........: 39796/57540 (69.16%)
Rejected.........: 0/39796 (0.00%)
Restore.Point....: 0/1 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:39795-39796 Iteration:960-1024
Candidates.#1....: PleaseSubscribe!toMyBlog -> PleaseSubscribe!toMyBlog
Started: Wed Jan 27 12:46:51 2021
Stopped: Wed Jan 27 13:29:57 2021
If you’re new to hashcat or want to understand how the flags on this operate, here’s the breakdown:
-a 0specifies an attack mode, with zero being the straight mode. This saying to use all words in a list.-m 3200specifies the hash type. As we researched earlier, this is a bcrypt hash which is number 3200 for hashcat.hash.txtthe file containing the hashes to be crackedwordlist.txtis the “dictionary” we’re using for our straight mode attack.-r Hob0Rules/d3adhob0.ruleis the rule we want to use, manipulating the words in the dictionary according to the rules in the file.-o cracked.txttells hashcat to write the cracked hashes to a file calledcracked.txt.-w 3sets the workload profile. Setting this to3gives a more tuned experice on your desktop, but it can also be slower. To utilize more of your GPU, use a workload setting of1, but your desktop will probably lag. The default setting is2.-Ois shorthand for--optimized-kernel-enable, this limits the password length.
Owning Root #
Remember, this is the password for the MatterMost account named root.
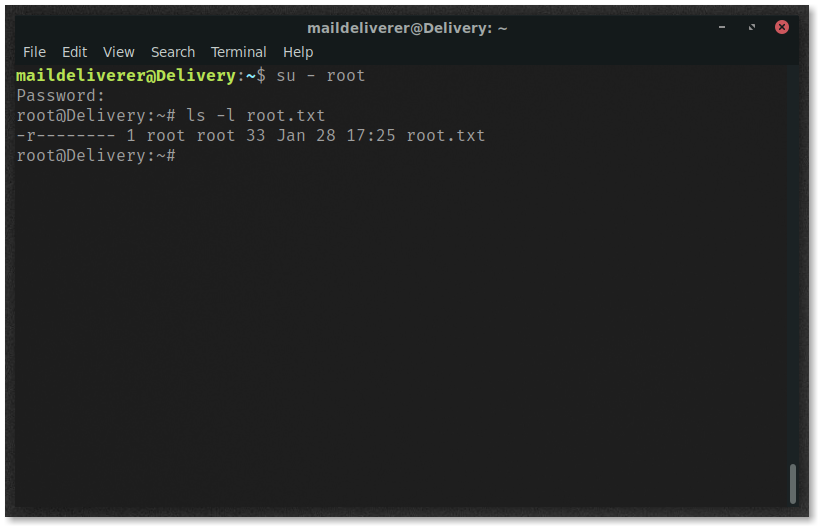
However, I’m going to try and hope that there is some password reuse here, and try to switch to the root user on the server using this new password.
su - root
Success!
Now it’s time to party!

Conclusion #
This box really opened up my eyes to one thing when enumerating a target: read, Read, READ. One thing I find myself doing is overlooking the content on websites, chat messages, emails, etc. This really reminded me that I don’t need to speed-run these challenges. Take my time, read the content, really enumerate. Delivery was really an exciting machine for me. Every step forward brought a grin to my face and really pushed my drive to get root on the machine.

